I’ve considered time tracking and I’ve tested several software solutions. Perspective matters - I’m a systems administrator, I prefer doing things through the command line, and my favorite programming language is Python. My recommendations will be biased. I also feel strongly about open source and free software, and I want full control of my own data. Solutions where I cannot download the source code is not considered, same if I need to send my data to some “cloud solution”.
Time tracking systems - general thoughts
Someone asked/told me “What time tracker software do you use? I use hamster, and would recommend that”. This caused me to fall into a deep rabbit hole, looking into hamster and other time tracking software. I started documenting my journey, and I will compile it into three blog posts:
- This blog post contains my general thoughts on time tracking.
- Next blog post compares different time tracking software.
- Last blog post will tell detailed experiences from using some ... [continue reading]
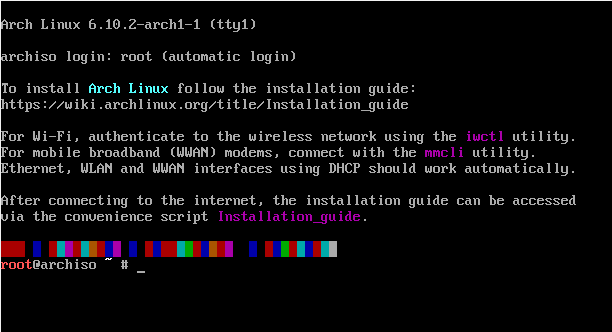
Creating and using a script to Install Arch linux through wifi
There are many different ways to create a bootable USB flash drive. I will in this guide, not show you how to create a bootable USB flash drive.
After rebooting your computer from the USB flash drive and when the installation medium’s boot loader menu appears
The default console key-map is US. You can change that using for example:
loadkeys sv-latin1 Use iwctl to connect to a wireless network (If you ... [continue reading]
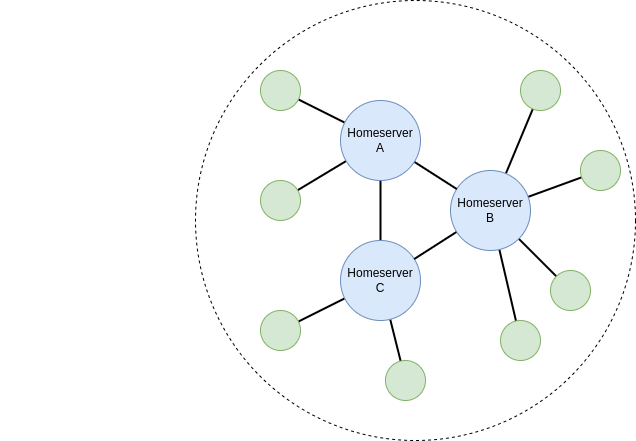
Kom igång med Matrix, skapa en Synapse server
I den här artikeln kommer vi att gå igenom hur man sätter upp en minimal installation av en Matrix homeserver med Synapse-implementationen. Denna server kommer att kunna federera med andra servrar, för att fullt ut delta i det offentliga Matrix-nätverket.
TLDR: Ifall du vill köra på snabbspåret, kika längst ner i artikeln, där finns det en sammanfattning som endast innehåller konfigurationsfilerna.
Introduktion
All mjukvara i denna ... [continue reading]
How to setup a Matrix homeserver
In this article we will cover how to setup a minimal installation of a Matrix homeserver using the Synapse implementation. This homeserver will be able to federate to other homeserver to completely participate in the public Matrix network.
TLDR: Look at the bottom of this article, there is a summary if you just want the configuration files.
Introduction
All software ... [continue reading]
Att bana väg för öppen källkod i offentlig sektor
Open source i offentlig sektor - utmaningar, möjligheter och vägen framåt.
Summering
Denna artikel beskriver processen och lärdomarna från att släppa ett API som öppen källkod inom offentlig sektor. Projektet, som utvecklades för digitala nationella prov (“DNP”), visar hur öppen källkod kan stärka samarbete, transparens och innovation. Artikeln lyfter fram både möjligheter och utmaningar – från säkerhet och juridiska aspekter till kulturellt motstånd – och ger insikter för andra myndigheter som överväger liknande initiativ.
Slutsatsen är att öppen källkod ... [continue reading]
Why automate Ansible
Ansible can be used for many things. There are only a few things I have on my bucket list of things I would like to do, where Ansible cannot help me.
One of my most urgent things to handle was the increasing complexity of Ansible, its configuration and in particular the role development. As I got deeper into Ansible, more and more factors needed to be taken into consideration when setting up a role: the role structure, linting issues, molecule ... [continue reading]
Comparison of different compression tools
Working with various compressed files on a daily basis, I found I didn’t actually know how the different tools performed compared to each other. I know different compression will best fit different types of data, but I wanted to compare using a large generic file.
The setup
The file I chose was a 4194304000 byte (4.0 GB) Ubuntu installation disk image.
The machine tasked with doing of the bit-mashing was an Ubuntu with a AMD Ryzen 9 5900X 12-Core ... [continue reading]
Why TCP keepalive may be important
Executive summary
- TCP connections may freeze due to network troubles, spontaneous reboots or failovers. The application should be robust enough to handle it.
- The concept of “TCP keepalive” is one way of solving it. Linux does not come with any knobs to turn it on globally, and by default it’s turned off - but there are workarounds.
- “TCP keepalive” needs to be configured according to the network; one may want slightly different configuration for communication between two servers ... [continue reading]
The irony of insecure security software
It can probably be understood from my previous blog post that if it was up to me, I’d avoid products like CrowdStrike - but every now and then I still have to install something like that. It’s not the idea of “security software” per se that I’m against, it’s the actual implementation of many of those products. This post lists up some properties that should be fulfilled for me to happy to install such a product.