This post appeared originally in our sysadvent series and has been moved here following the discontinuation of the sysadvent microsite

This post appeared originally in our sysadvent series and has been moved here following the discontinuation of the sysadvent microsite

It’s easy to get lost in Windows large event logs and log files during troubleshooting, here to help are PowerShell cmdlets Get-EventLog and Get-Content.
These cmdlets shows PowerShell’s strength comparing to the built-in GUI-tools in Windows. Let’s start with cmdlet Get-EventLog to get some information from an event log. Examples below is how I often work with these cmdlets when searching for logged events on hosts.
Start PowerShell from a command prompt by typing powershell.exe or enter powershell.exe in run command window.
View five newest events that been logged and display output as an list with fl/format-list.
Get-Eventlog -Logname System -Newest 5 | fl
View only error and warning events, use parameter “EntryType”.
Get-EventLog -LogName System -Newest 10 -EntryType Error,Warning | fl
EventID can be useful information to have, to get it we need to select the objects we want to view from an event. Has also changed search area to after an entered date.
Get-EventLog -LogName System -After 2016-11-24 -EntryType Error,Warning | select-object TimeWritten,EntryType,Source,EventID,Username,Message | fl
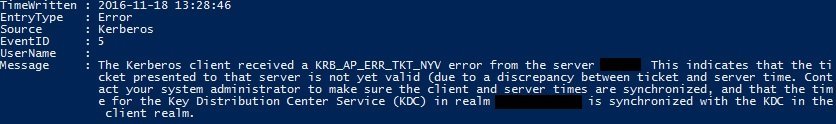
To find events that have equal values, you can use ‘Where-Object’. Results will only display if Event ID is 10016 and EntryType equals error.
Get-EventLog -LogName System -After 2016-11-24 | Where-Object {$_.EventId -eq 10016 -and $_.EntryType -eq 'Error'} | fl
Do this remotely to an host is comfortable when you switching between different ones, use parameter ‘ComputerName’. You can enter multiple hosts or create arrays.
Get-EventLog -ComputerName host1.web.com -LogName System -Newest 50 | Where-Object {$_.EventId -eq 10016 -and $_.EntryType -eq 'Error'} | fl
Let’s filter out this even more by using time ranges when searching for events,this is perfect to use when have you large quantities during a day. The event we are looking for is between 11:00 to 11:30 on specified day.
Get-EventLog -LogName System -After ([datetime]'2016-12-08 11:00') -before ([datetime]'2016-12-08 11:30')
OK, but there’s still a lot of events I don’t want read through. An option is to match a value to what the event message contains, I’m not viewing output with fl/format-list this time.
Get-EventLog -LogName System -After ([datetime]'2016-11-24 11:00') -before ([datetime]'2016-11-24 11:30') | Where-Object {$_.message -match "service entered the stopped state"}
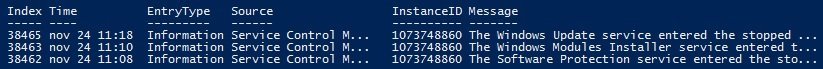
Large log files can be really annoying to handle if you only have an basic text editor available. PowerShell’s cmdlet Get-Content can relive some pain for you when working with thousands of lines.
To not get entire content of an file in console window, select only last 10 rows from the end.
Get-Content .\IISwebsite.log -tail 10
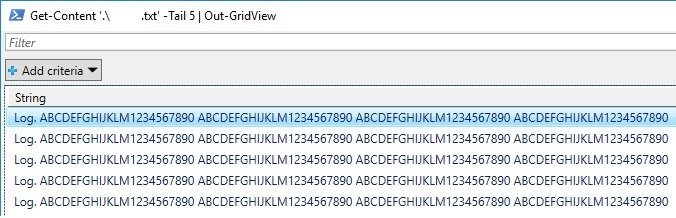
Depending on log files structure it still can be a mess for your eyes to read it in console window, send your output with ‘Out-Gridview’ to view it in a grid window.
Get-Content .\IISwebsite.log -first 15 | Out-Gridview
Pick up strings in log files is also useful. Select all strings containing “HttpError”.
Get-Content .\IISwebsite.log | ? {($_ | Select-String “HttpError”)}
When located logged information and want to export selected strings to a new file.
Get-Content .\IISwebsite.log | ? {($_ | Select-String “HttpError”)} | Out-file 'path\file.log'
Update
Tekton is a neat Kubernetes native CI/CD system. In this article we will explore what Kubernetes native means and show how this allows us to implement CI/CD features that are not present in Tekton itself by leveraging the power of the Kubernetes API. As an example, we will show how to ensure that Pipelines do not run in parallel.
... [continue reading]